Azure Identity Protection
Azure Identity Protection is a feature of Microsoft Enterprise Mobility + Security and is a premium feature in EMS E5. We conducted a test to see if a user would be blocked while trying to log in from 2 separate locations.
We went to https://portal.azure.com/ and logged in with credentials normally from our home office server. I then created a 2012 Server virtual machine setting up and configuring Active Directory and azure AD Connect.
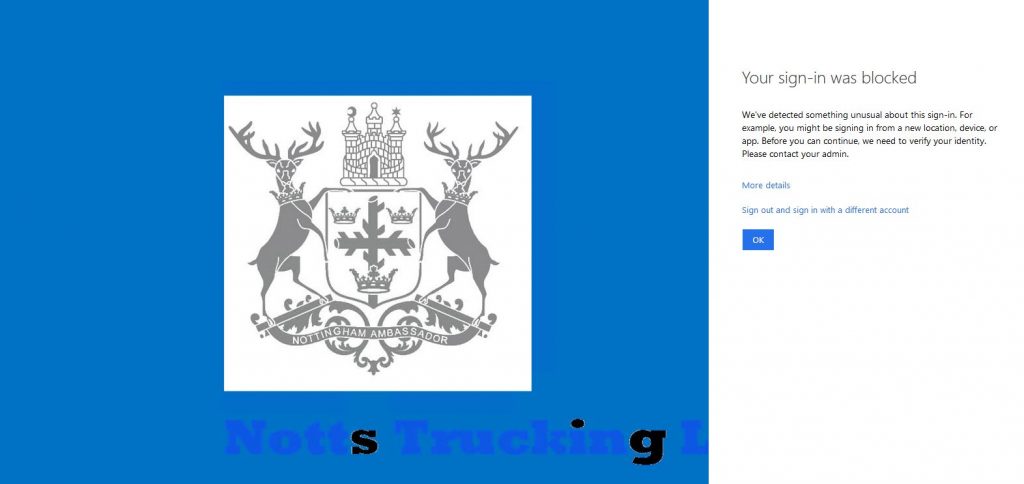
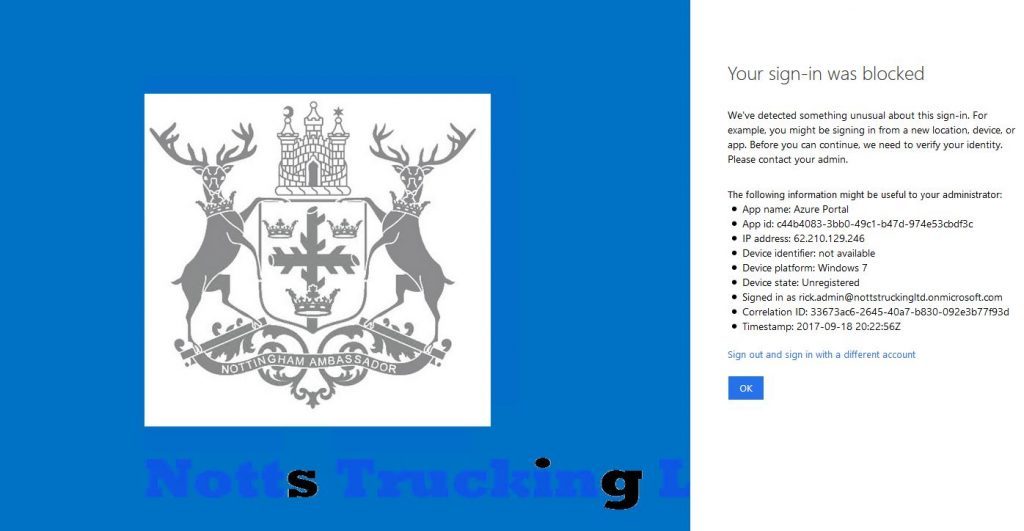
Using the Tor browser I went to portal.azure.com to login with the same user a 2nd time.
Our Results
Your sign-in was blocked
For example, you might be signing in from a new location, device, or app.
Risky sign-ins
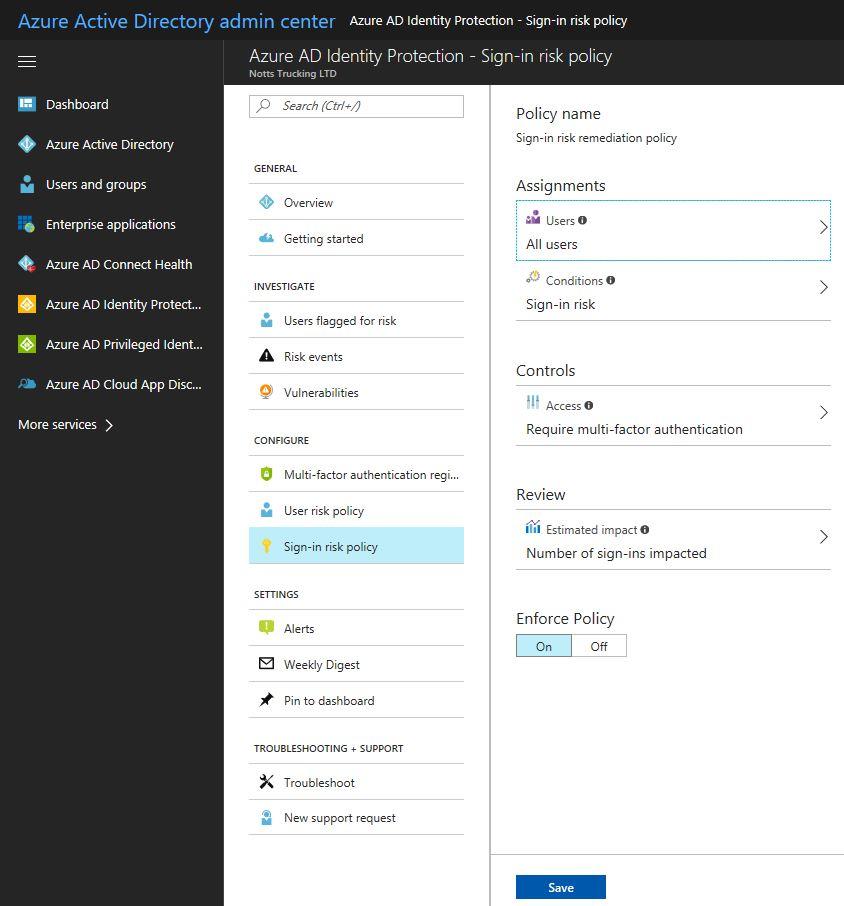
Azure Active Directory detects risk event types in real-time and offline.
Each risk event that has been detected for a sign-in of a user contributes to a logical concept called risky sign-in.
A risky sign-in is an indicator of a sign-in attempt that might not have been performed by the legitimate owner of a user account.
