Identity Types within Azure AD
There are four identity types within Azure Active Directory
The variations of each identity type and the benefits and use cases:
- User
- Service Principal
- Managed Identity
- Device
User identity – a representation of an entity that is managed by Azure AD both employees and guests are represented as users. A guest is external to the company, like a business partner or vendor collaborating with employees. Azure AD (B2B) business-to-business collaboration: A feature within external Identities that includes the capability to add guest users. Enables organizations to securely share applications and services with guest users from other organizations.
Service Principal – An identity for an application, Enables features like authentication and authorization of the application to resources that are secured by the Azure AD tenant. An application must first be registered with Azure AD to enable identity and access integration. Once registered, a service principal is created in each Azure AD tenant where the application is used to enable authentication and authorization in resource access.
Managed Identity – A special type of service principal that is automatically managed in Azure AD. This eliminates the need for admins and developers to manage credentials. Managed identities come in two varieties.
User-assigned – which can be shared by multiple resources and has a lifecycle independent of these resources. eg: (You could assign this user-assigned ID to many virtual machines).
System-assigned – which is tied to the lifecycle of a specific service or resource and cannot be shared. eg: (when the system or resource is retired and deleted that system-assigned identity is deleted with it).
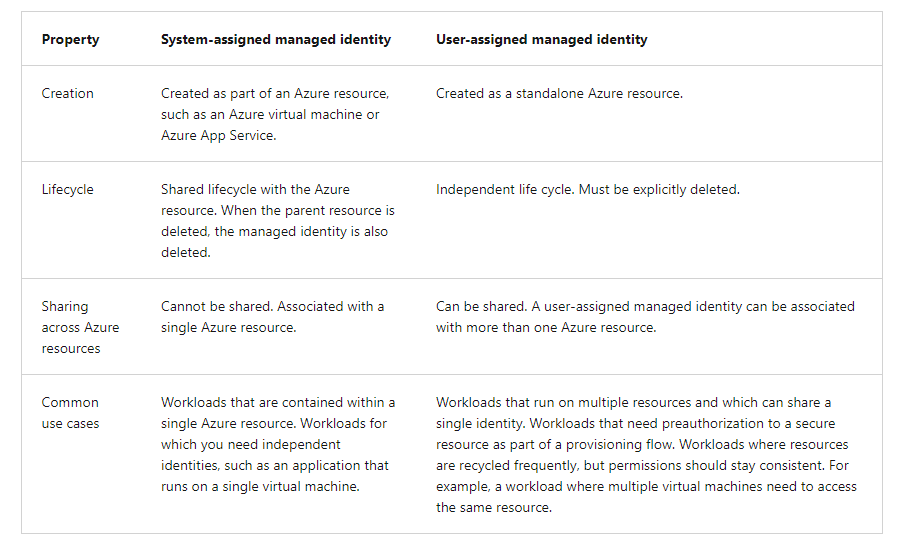
The preference when you have a choice would be to use system-assigned managed identities over user-assigned as they minimize our administrative effort.
Device Identity – entities can be:
Azure AD-registered – provides users with support for bring-your-own-device (BYOD) mobile device scenarios.
Azure AD-joined – A device joined to Azure AD through an organizational account, which is then used to sign into the device.
Hybrid Azure AD-joined – Domain joined to Azure AD and on-premises Active Directory.
Benefits of Device registration
- Single sign-on (SSO) – registering and joining devices to Azure AD gives users single sign-on (SSO) to cloud-based resources.
- Azure AD-joined devices also benefit from the SSO experience to resources and apps that reply on on-premises Active Directory.
- Device Management – registration enables device management options with Intune to control how an organization’s devices are used.
Mobile device management (MDM) for company-owned devices
Mobile application management (MAM) for personal devices. (BYOD)
Overview of the Hybrid of the Hybrid Identity Model
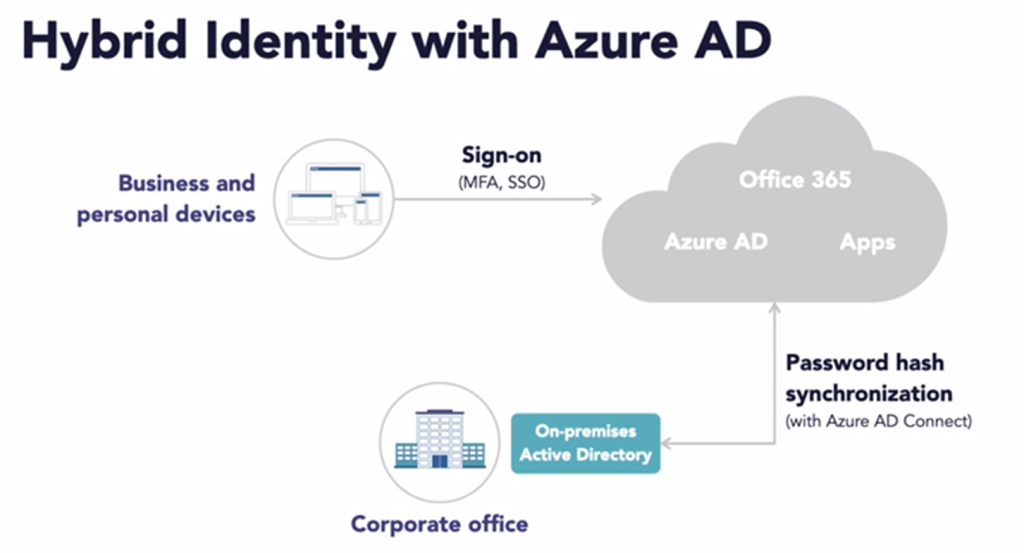
All of these scenarios require an on-premise Active Directory (source of truth).
Azure AD password hash-synchronization – The simplest way to enable authentication for on-premises directory objects in Azure AD. The user is authenticated by Azure AD.

Azure AD pass-through authentication (PTA) – While password-hash is synchronized to Azure AD, the user is authenticated directly against your on-premises Active Directory. Can be used to enforce Active Directory restrictions not present in Azure AD, like “login hours”.

Azure AD Federation authentication – Authentication for organizations that need advanced measures not currently supported in Azure AD, like smart cards and certificates. Again, Azure AD passes the request to on-premises Active Directory.

Why are External Identities Necessary?
- Employees today are more commonly working with people both inside and outside of their organization.
- External users (vendors, partners) may need access to resources inside your organization.
- Azure AD External Identities is a set of capabilities that enables organizations to allow access to external users.
Types of External Identities
Enable your customer’s partners, and other guest users to “bring their own identities” to sign in.
Two different types of Azure AD External Identities:
B2B (business-to-business) – collaboration allows you to share apps and resources with external users.
B2C (business-to-consumer) – is an identity management solution for consumer-facing apps.
Azure AD B2B (business-to-business) – Enables organizations to share apps and resources with guest users from organizations, partners and collaborators use their own identity management solutions, so there is no external admin overhead:
- Uses an invitation and redemption process.
- Can perform SSPR through their usual process. (identity is managed elsewhere).
- Admins can also enable self-service sign-up user flows to allow external users to sign up without admin intervention.
Azure AD B2C (business-to-consumer) – Enables external users to use their preferred social, work, or local identities for single sign-on to an organization’s apps. External users are managed in the Azure AD B2C directory, separately from the organization’s employee and partner directory.
- A customer identity access management (CIAM) solution.
- Supports millions of users and billions of authentications per day.
- Automatically handles threats like denial-of-service, password spray, or brute-force attacks.